Title
Situation
This case study highlights a real-world cybersecurity incident that could occur in contemporary enterprise networks.
A company experienced network outages and performance degradation, which significantly impacted its Operational Technology (OT) manufacturing network. The attack vector originated from an ISP’s infrastructure, allowing the adversary to progressively move closer to industrial control systems and the organization’s central database.
Attack Progression
- Reconnaissance Phase: The attacker employed a “spray and pray” tactic, scanning multiple targets indiscriminately in search of vulnerabilities. Using automated scanning tools, the attacker probed exposed services on public IP ranges. High-interest targets included remote management interfaces (SSH, Winbox, and Telnet), outdated web applications, and network infrastructure devices.
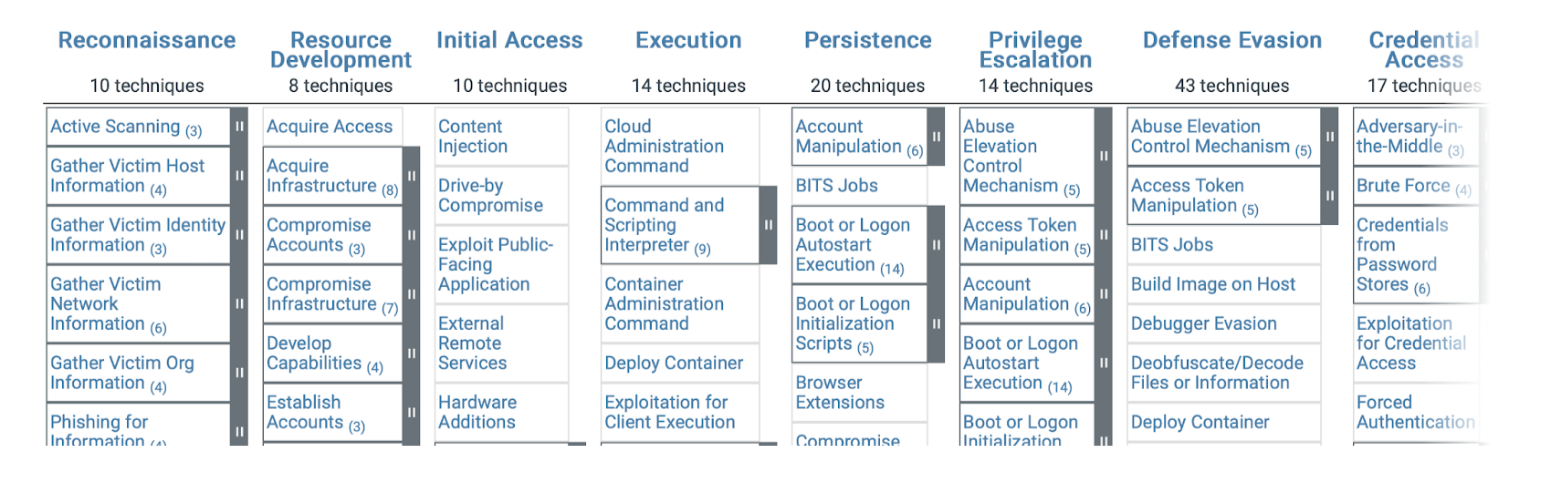
Picture: MITRE ATT&CK® Matrix: visualization of attack phases
- ‘’Initial Access: The ISP operated RouterOS-based devices, one of which was compromised due to an outdated firmware vulnerability. The attacker exploited CVE-2022-45315, a vulnerability allowing unauthorized execution of code via specially crafted SNMP packets. The exploit provided a foothold into the ISP’s core network, allowing the attacker to execute commands remotely and establish persistence.
- Privilege Escalation & Establishing Persistence: Once inside, the attacker elevated privileges by exploiting weak credentials and misconfigured access control rules. They also deployed custom scripts to maintain access even after system reboots.
- Lateral Movement: The compromised ISP router began brute-force attacks on Telnet, SSH, and Winbox services on other network devices. The attacker attempted to map the ISP’s internal network structure, identifying routers, firewalls, and enterprise edge devices that could be leveraged for further exploitation.
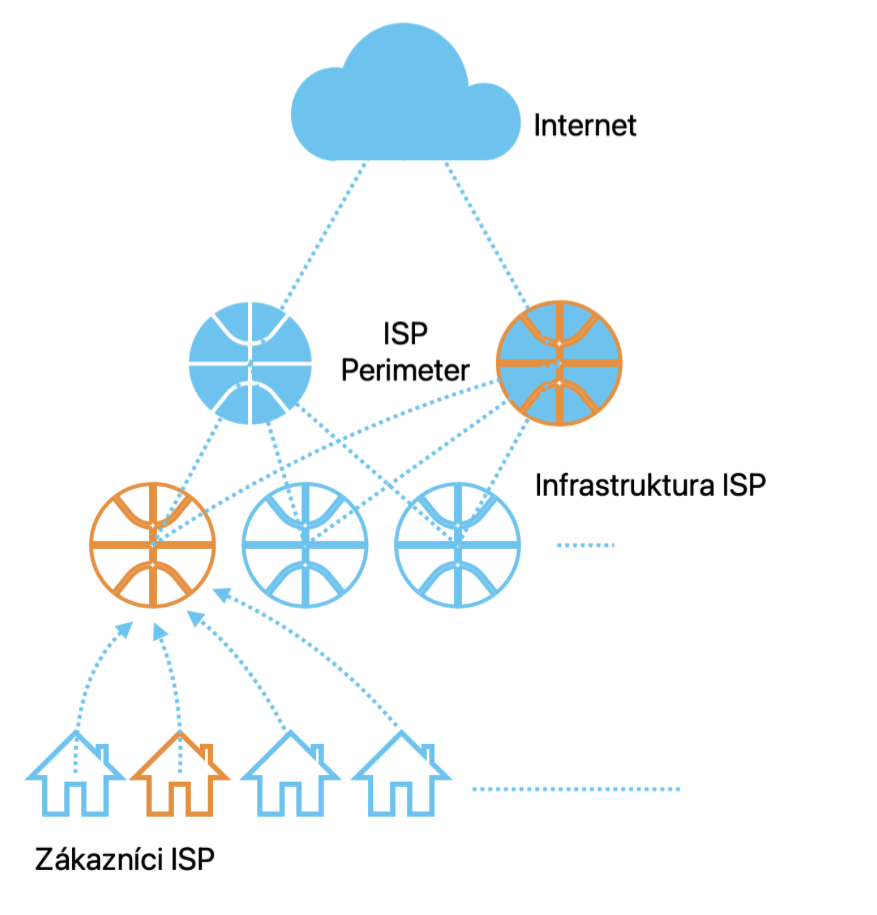
Picture: MITRE ATT&CK® Matrix: visualization of attack phases
- Enterprise Network Compromise: The attacker successfully took control of the enterprise’s perimeter router, establishing communication with Command & Control (C2) servers. They used DNS tunneling and encrypted HTTP requests to mask malicious activity and avoid detection by standard firewall monitoring.
- OT Network Intrusion: The attacker attempted to compromise the perimeter of the OT network, initiating brute-force attacks on the enterprise’s database servers and performing slow, targeted scans against OT network segments, probing for vulnerable** devices**. However, the attack was detected at this stage due to volumetric NetFlow analysis, and mitigation efforts were implemented before a full breach occurred. The intrusion detection systems (IDS) regerated abnormal amount of logs and this triggered alert, allowing network administrators to block the attack and temporarily isolate the attacked network before incident was revealed and attack mitigated.
Challange
Challenges cover detection of such incidents
- Firewall monitoring failed to detect the attack since the adversary leveraged a trusted ISP infrastructure to move laterally.
- Absence of Endpoint Detection and Response (EDR) across all systems limited forensic reconstruction of the attack sequence.
- Attack on OT network activity remained nearly undetectable, as it was performed gradually and from trusted devices.
Solution
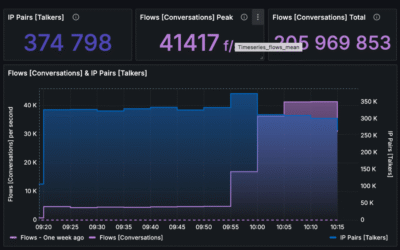
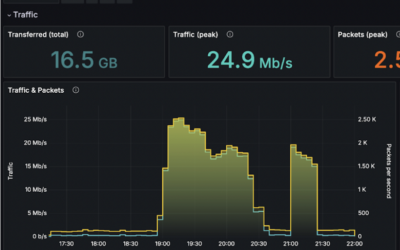
- Deployment of NetFlow analysis at the ISP level helped reveal abnormal traffic patterns.
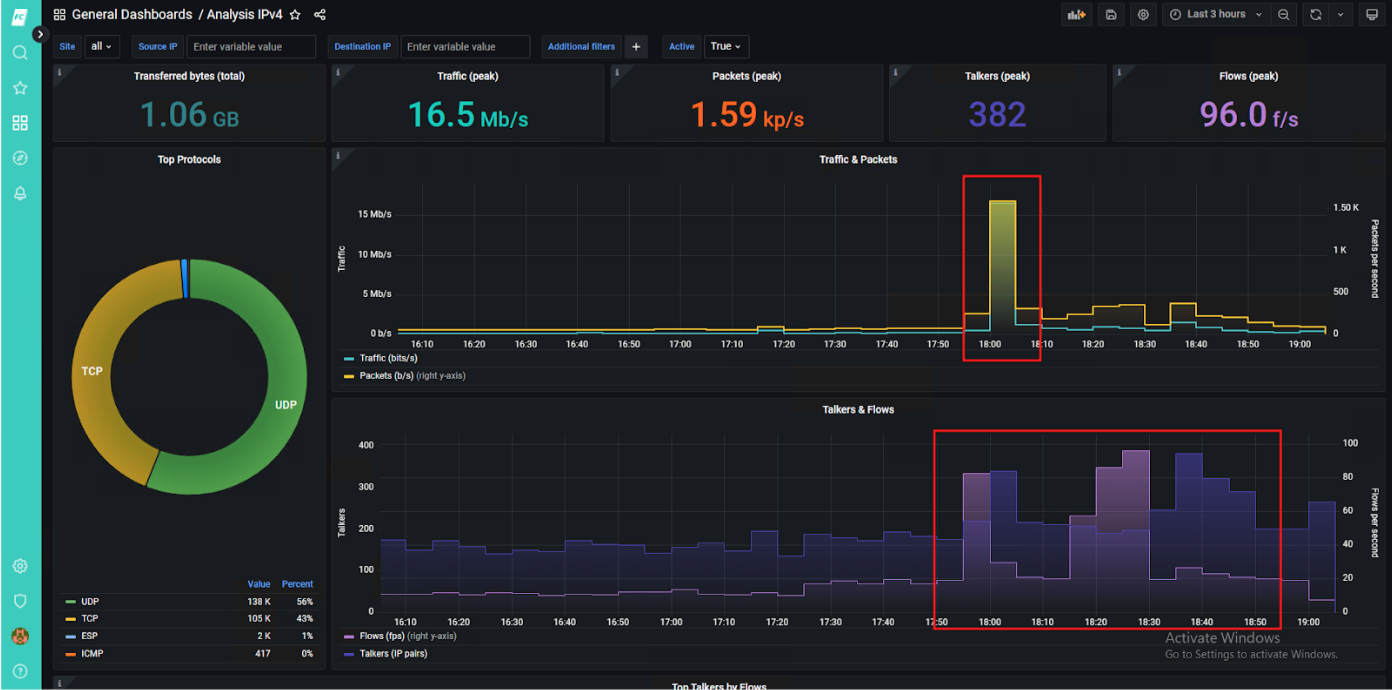
- Correlation of multiple data sources is the key for early detection: NetFlow data, Vulnerability scan, Intrusion Detection System (IDS) logs, usage of IP reputation and threat feeds, and DNS telemetry.

- NetFlow data helped to reconstruct the incident and decide on how to improve security posture.
- Cleanup mainly consisted of a) better isolation (segmentation) of network devices, and **b) updating ** all infected devices.
- Monitoring of both ISP and enterprise infrastructure, namely regular vulnerability scans and update status of all key devices.
Results
By leveraging advanced network analysis, data correlation, and proactive monitoring, security teams were able to detect the attack before critical OT assets were compromised. This case study underscores the importance of collaboration between ISPs and enterprises in fortifying cybersecurity defenses.
Resources
- Netflow analysis in Grafana
- Anomaly detection
- Flow enrichment with IP reputation
- Vulnerability scan
- Integration of DNS security solution data feed
- Integration of IDS logs in Grafana
Takeaway
✅ Firewall monitoring alone is insufficient—NetFlow data provides deeper insights into traffic flows.
✅ Proactive security measures at the ISP level can prevent attack propagation.
✅ Network segmentation and multi-source log correlation enhance detection capabilities.
✅ Attacks often exploit the weakest link—in this case, vulnerabilities within ISP infrastructure.