Title
Carpet bombing of many ISPs revealed differences between reactive and proactive approaches.
Situation
In May 2025, there were a series of DoS (Denial of Service) attacks targeted at hundreds of European ISPs. Attacks were in the form of TCP SYN Flood and targeted the whole IP range of an operator, not just one IP or just one service. Length of the incident varied between 2 and 40 minutes. However it happened repeatedly, several times a day and for a few days in a row.
During the attack CORE routers were overwhelmed by the number of incoming connection attempts. It resulted in internet outages for the whole operator’s customer base.
Challange
Most of the ISPs decided to wait it out until the attack was over hoping their customers won’t complain much.
Some decided to understand the attack and be prepared for the next time.
The issue is that common NOC monitoring tools are based on SNMP tools such as Zabbix. Unfortunately these tools don’t contain necessary signals to uncover:
- Who is an attacker
- What method was used to attack
And consequently the ammunition that is needed for attack mitigation is missing.
What to do?
Solution
This is exactly where netflow data comes in handy. FLOWCUTTER netflow analysis and anomaly detection is a perfect fit for such a problem.
Customers that exported netflow from their CORE routers to FLOWCUTTER were able to analyse the attack and mitigate it easily.
Results
See the finding of this particular instance of a DoS attack.
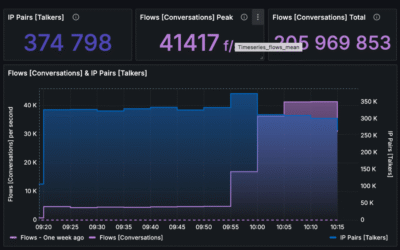
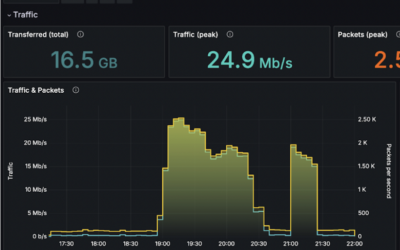
The operator was able to observe an anomaly in connection attempts (flows per second). It raised 10 times when compared to normal behavior before an attack.
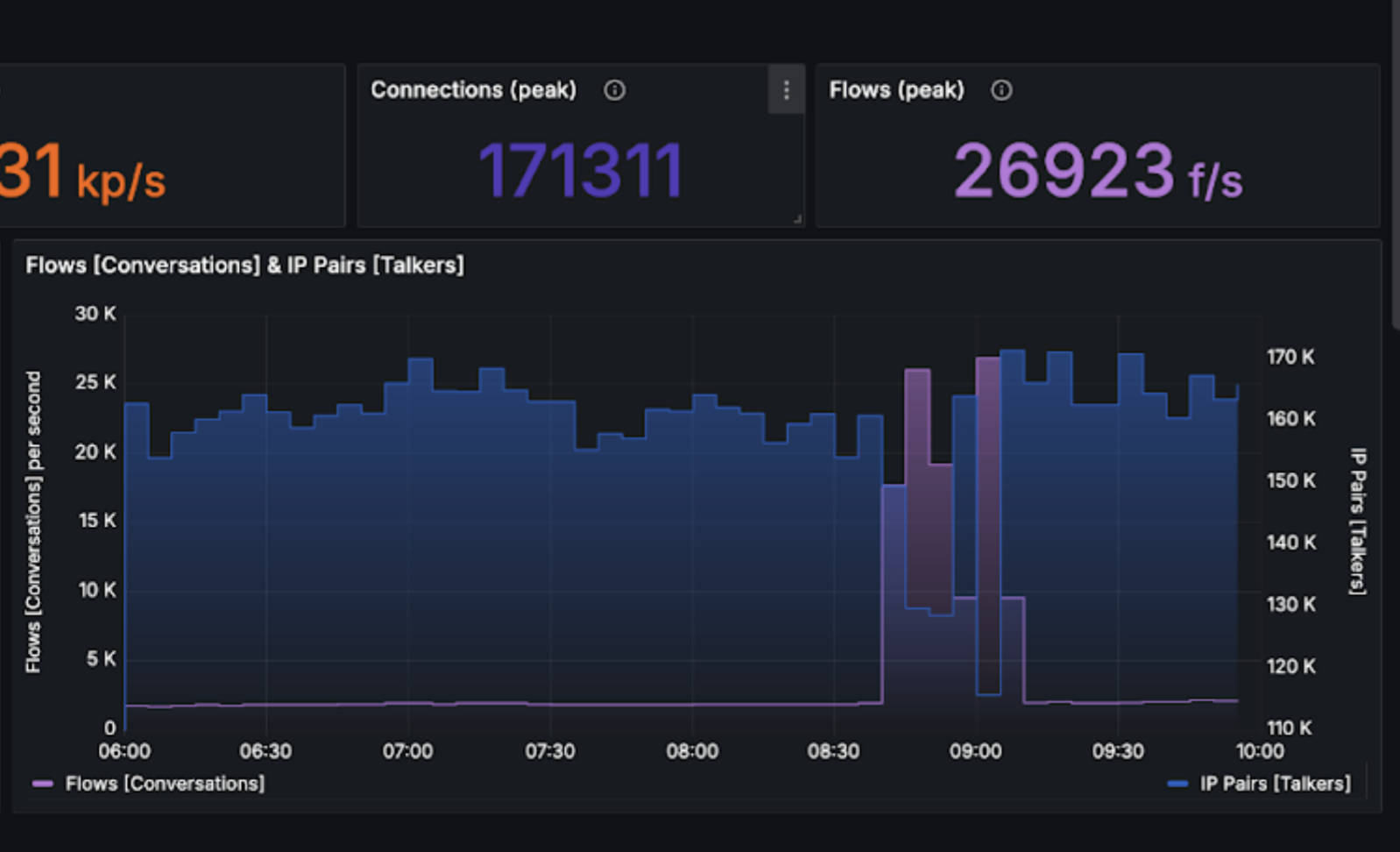
When operator zoomed in the time interval of the anomaly, he was able to clearly see attack vector.
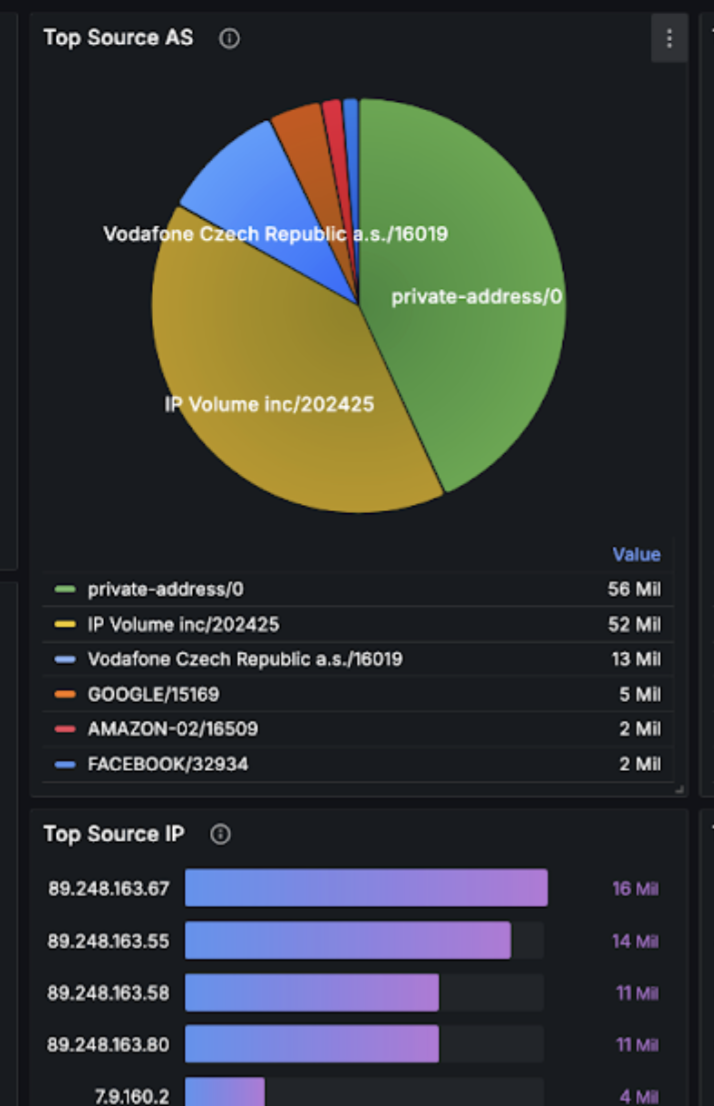
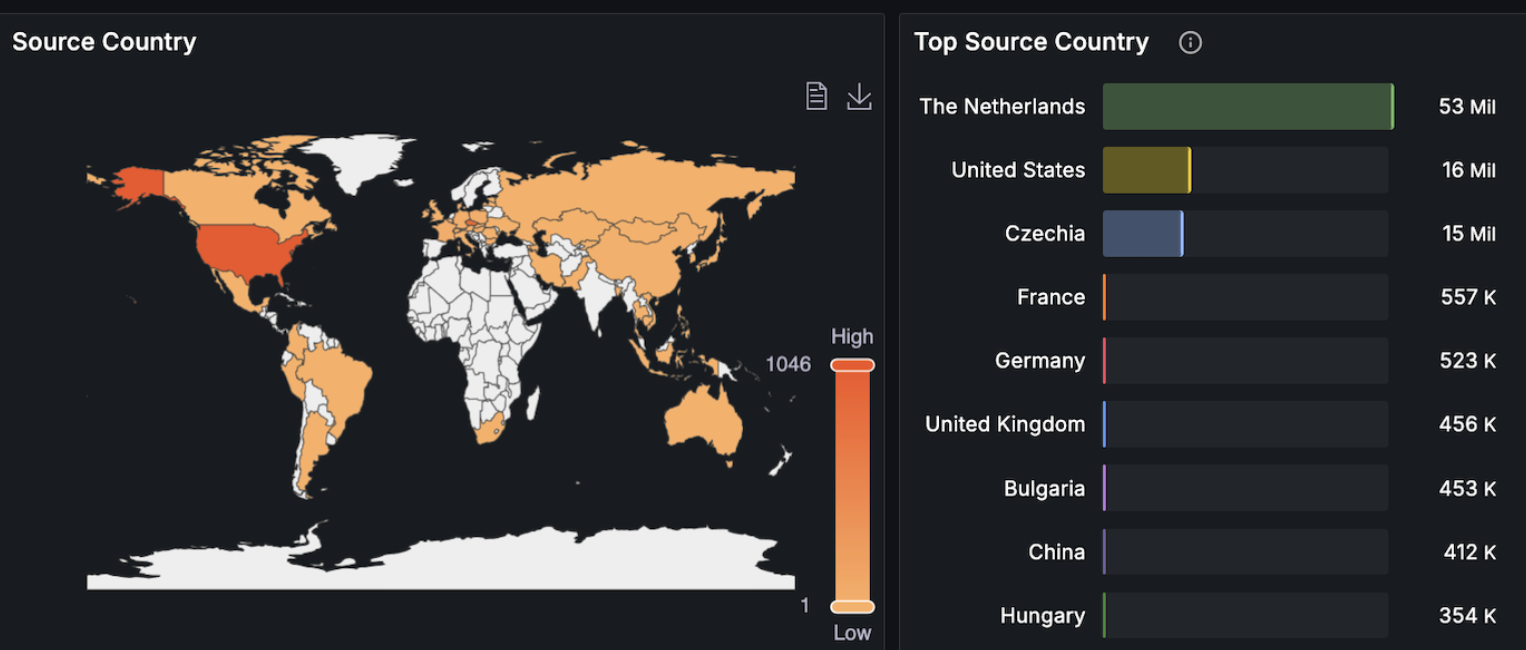
It came from AS 202425 headquartered in the Netherlands with 4 IP addresses being responsible for the flood. Also an attack method was revealed: SYN Flood from a few source ports.
ISP mitigated the next attack either by refusing traffic from this AS or just denied connections from particular IP addresses.
Note that even though in this case source port information wasn’t necessary for mitigation, if this was a distributed DDoS attack, then source port would be the key to mitigate it using BGP Flowspec.
Resources
- Netflow analysis in Grafana
- County and ASN enrichment
- Flow-based (D)DoS detection
Takeaway
ISPs that chose the pro-active approach were able to quickly and easily determine who was attacking them and how, Consequently the next wave of attacks didn’t influence them at all.
ISPs with a reactive approach had to wait it out.
Testimonials
“First time this flood attack hit us, it caused short outage. With FLOWCUTTER we were able to identify attacker fast and mitigate it.“